Solution Accelerators
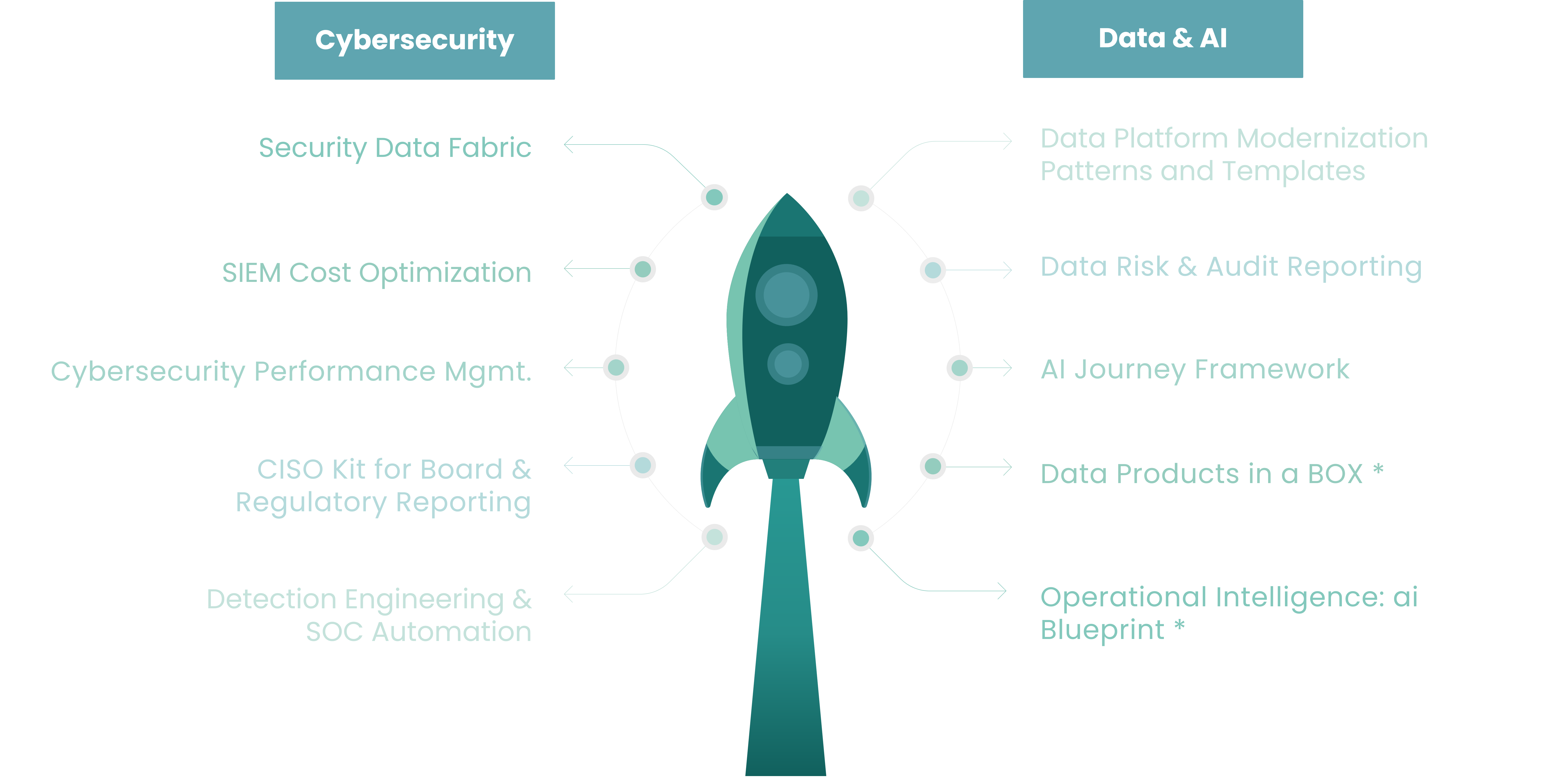
Sarral's IP - AI in action for Cybersecurity Use cases
CDAO Quick Wins
Lack of enterprise-wide data & AI strategy
Data & AI Strategy Blueprint
Define priorities, roadmap, and execution plan
- Clear roadmap
- Accelerated AI adoption
Disconnected data initiatives & silos
Data Product Strategy & Value Framework
Prioritize, design, and measure data products
- Productized delivery
- Traceable value
- Scalable realization
Fragmented GenAI experiments & security concerns
Enterprise GenAI Architecture
Unified, reusable, secure RAG & agentic workflows
- Unified platform
- Consistent security
- Accelerated innovation
Unclear AI roadmap for data management
AI-Driven Data Management Modernization
Automate cataloging, lineage, and stewardship
- AI-powered metadata ops
- Faster discovery
- Less manual effort
Limited data governance & regulatory visibility
Data Risk & Governance Accelerator
Link usage, lineage, and compliance workflows
- Continuous risk visibility
- Faster regulatory response
Sensitive data exposure in AI workloads
Responsible AI Data Security Strategy
DSPM-led security, classification & controls
- Secure foundation
- Reduced shadow AI
- Leakage risk reduction
Fragmented platforms & tool sprawl
Platform Architecture Rationalization
Consolidate tools, modernize insight delivery
- Lower TCO
- Faster engineering
- Better adoption
Complex platform migrations
Migration Strategy & Accelerator Kit
Future-state design & rapid migration patterns
- Clear roadmap
- Faster execution
- Lower migration risk
Unclear operational roles in AI delivery
Operational Model for AI & Analytics
Define roles, flows, and platform enablers
- Faster deployment
- Clear accountability
- Better collaboration
CISO Quick Wins
No unified, real-time visibility into security controls & regulatory readiness
Regulatory Gap Remediation Accelerators
Link telemetry, GRC states, findings, and compliance workflows
- Faster regulatory closure
- Real-time control visibility
- Evidence aligned to standards
Unclear AI adoption strategy & data security risks
AI Readiness Assessment
Methodology, prioritized roadmap, and security risk review
- Accelerated AI deployment
- Secure, compliant adoption
High security tool costs & overlapping capabilities
Technology Rationalization & Optimization
Consolidate platforms, streamline dashboards, and optimize spend
- Lower costs
- Stronger security posture
- Reduced operational burden
Rising SIEM costs & low SOC productivity
Security Visibility & Cost Optimization
Assess and modernize SIEM/logging architecture
- Cost reduction roadmap
- Improved visibility
- Better SOC efficiency
Fragmented security data across systems
Security Data Pipeline & Data Lake Design
Unified pipelines, enrichment, and observability
- Improved threat detection
- Faster incident response
- Fewer false positives
Scalable analytics & GenAI for advanced detection
Security Data Lake & GenAI Architecture
Centralized platform, pipelines, and ML-driven detection
- Scalable storage
- GenAI-powered analytics
- Cost-effective retention
Lack of security metrics & board-level reporting
Security Performance Management (CISO Kit)
Dashboards, KPIs, and automated compliance reporting
- Better insights
- Improved board confidence
- Regulatory readiness
SOC overwhelmed by SIEM/SOAR noise
SOC Noise Reduction with GenAI
AI-driven design and deployment framework
- Reduced noise
- Faster detection & response
- Higher analyst efficiency
Limited understanding of compliance posture
Compliance Assessment
Gap analysis, remediation roadmap, and certification alignment
- Reduced compliance risks
- Streamlined audits
- Faster certifications
Cloud migration security challenges
Cloud Security Architecture
Baseline hybrid security design and control rationalization
- Unified cloud security
- Optimized controls
- Simplified operations